
Interviewing is like climbing a mountain, one mistake and you might have to start your journey from the beginning all over again!
Landing a new position is nearly a full-time job in itself. It can be time consuming, challenging, decreasing your confidence, affecting your motivation.. But like climbing a mountain, it won’t happen by accident, it has to be intentional, carefully working one step after another. One mistake and you might fall down to the bottom, and have to start from the first step again. So, like every complex tasks, one will need to prepare himself carefully to ensure the best completion to the journey forward.
In the following article, the most command tips and questions for interviewing in the software engineering field will be listed to help land that next big job!
Contents
Disclaimer
Being notoriously not a good interviewee myself, the following notes were gathered from previous experiences and past failures may enlighten on the process to not repeat the same mistakes when going through the job application. Use at your own risk, I won’t accept any responsibility for any missed opportunity, but will gladly take any credit for a new position landed using this guide!!
Interview Process
Phone screening
A screening interview is a type of job interview that’s conducted to determine if the applicant has the qualifications needed to do the job for which the company is hiring. A screening interview is typically the first interview in the hiring process, and it is usually conducted over the phone.
Technical Interview
The technical interview will be preparing yourself for the role you are applying. Brush up your skills, find online coding exercises, research the common questions asked on this company, and ensure you are able to answer swiftly about any details from the CV you forwarded to the recruiter.
More information is described in the preparation section below.
Coding Exercise
A coding exercise is usually the following step in the recruiting process.
This step can be conducted over a shared document, an online coding tool such as CoderPad or some similar tool. The exercise is made of few questions increasing in difficulty with the progress, but which are building on each other. The interviewer will want to hear your thinking on how to implement the problem before you start coding, so he can follow your reasoning. As a two-ways conversation, you iwll receive feedback as you implement. Once a question is completed, you will be asked how to improve your code, if it is efficient, and it time complexity and memory foot print.
It demonstrates your ability to code, but also your logical thinking, how you express yourself, and your understanding of other constraints that can affect scalability due to poor coding.
Assignment
Weekend or week-long assignments are getting more popular in the industry and it slowly starts to replace or complete the coding interview.
It demonstrates if someone is detail-oriented, if they can think out of the box, how good the programming language is grasped, how well you can do test-driven development. Additionally, these exercises are reflective of the kinds of projects you would expect in the position you applied, highlighting for both parties faily quickly if the candidate is a good fit for the position, and vice-versa, which is really valuable to discover before signing a contract.
Meeting
This is likely the last step in the recruiting process before receiving a job, congratulations for reaching this point! This step consists of meeting number of individuals from the team you are joining in addition to a manager or and HR representative. It can vary in format, from the face-to-face meeting, to the whiteboard coding to explain your understanding of algorithms, in addition to written coding exercises. The format will need to be clarified in advance, with its length, and the required dress code, formal (suit and tie) or smart casual, but always neatly dressed and on time.
Do your homework, and research the company and the typical questions and the usual meeting format. You will also need to prepare for open-ended questions, and behavioural questions, by answering using the S.T.A.R. method. Take the time to listen, and be prepared for questions deep in the corresponding programming language, and be prepared to answer any item from the CV you forwarded. For this reason, be careful to not over sell yourself in your CV as you may be interrogated on every aspect of it. Finally, you will be given the opportunity to ask questions yourself, this is an opportunity to demonstrate your interest for the role and ask prepared question you might have.
Preparation
General Advices
Preparation is important at each stage of the interview, in various amount, increasing progressively as you go through the steps of the process. Therefore, some homework is required at each stage of the process.
First of all, it is needed to ensure the company business model is understood correctly, if it corresponds to the aspirations of the candidate, and that the products and services are known enough to have a constructive conversation with your interlocutors. In particular, the products related to the team applied needs to be well researched.
Also, some preparation is needed to tailor some answers on the interest towards the particular field or role you are applying for or role is also useful. Sample experiences from previous roles relating to the applied position is needed to display a compatibility with the team you are hoping to join.
Finally, ensure your phone and laptop are fully charged, that your internet connection is working correctly, that your communication tools (HangOut, Skype, etc.) are correctly configured, and that you can speak freely in a quiet and undisturbed area.
S.T.A.R. format
The S.T.A.R. format is a method to articulate your answers to generally open-ended questions to give a nice and concise happy ending to a challenging situation you have encountered in the past. The candidate describes the challenge, its resolution, the positive effect, and finally the business outcome. This acronym stands for:
- Situation
- Task
- Action
- Resolution
Especially for the open-ended questions and behavioural questions, it’s important to prepare an example in advance using the S.T.A.R format, to allows structuring the general shape of a response without being caught too much off-guard, especially after focusing only on the positive during the rest of the interview.
Open-ended questions
The open-ended questions don’t have a right or a wrong answer like technical questions. These questions are an invitation to talk about yourself and allows you to steer the conversation towards an achievement you want to highlight. The answer should be articulated around the S.T.A.R. approach and focus on the outcome. There’s many examples of open-ended questions, but the answer should emphasise what value was added for the company. A few common questions are:
- Why should we hire you?
- Why are you interested in this position?
- Describe your greatest accomplishment at work.
- Tell me about the biggest mistake you’ve made, how you would do it differently, and what did you learn from this experience?
- Give me an example of when you’ve had to go above and beyond the call of duty to get the job done.
- Give me an example of a situation when you’ve had to deal with a very difficult colleague, and how did you deal with it?
Questions to ask
During the interview, you will have the opportunity to ask further details about the role or the company. You can as well prepare questions such as some of the commons ones below:
- What are the challenges of this position? What do you like best about working for this company?
- What qualities are the most important for doing well and advancing at the firm?
- Can you give me example of how I would collaborate with my manager?
- If you were to hire me, what might I expect in a typical day?
- How do you help your team grow professionally?
GitHub Projects
In the past, many projects worked on by an engineer would have been proprietary and confidential so that the code couldn’t leave the premises to show to potential recruiter. But nowadays, everyone can contribute to open-source software, host their pet projects, show the results from a bootcamp in a publicly available GitHub (or GitLab) repository. This is a great way to show off your code, your respect code convention, your familiarity with object-oriented programming, multi-threading, unit testing…
Be prepared to show this to improve the perception of your profile, and maybe create a sample project using the technologies for he position you are applying to demonstrate your abilities and be better prepared for the technical interview.
Technical interview
The following categories provide some sample area you might be interviewed on during the technical interview or the meeting itself. It is important to be prepared for any questions related to the position you are applying or which is mentioned on your CV.
Programming
Scalability
Scalability of services can be achieved by using well performing algorithms (see Big-O Notation), and creating a service based on a distributed architecture using caching and redundancy to provide resiliency and quality of service. Some good examples are how Google do Planet Scale Services and Netflix Scalable Microservices.
Big-O Notation
Big-O notation is a relative representation of the complexity of an algorithm. It allows understand the computational complexity which is essential to design scalable algorithms, applications and systems. In practice, it allows to assess what are the potential bottlenecks in a program or service. The following resources are thorough explanation of the Big-O Notation:
Race Condition
A race condition occurs when two or more processes try to access the same data concurrently or performing the same operation concurrently.
Inheritance
In object-oriented programming, inheritance is a way to reuse code of existing objects. It’s good when you want to establish a subtype from an existing object. Objects are defined by classes, classes can inherit attributes and behavior from pre-existing classes. The resulting classes are known as derived classes or subclasses.
Java
Java is a popular programming language both in academic and in professional environment. It is stable, complete, is supported by very good IDE, and provides good Object-Oriented support. To prepare for this section of the interview, it is important to review the basics as well as most complex use cases.
There are many online resources on this topic; the following resources will get you started with most of the required information: Java Interview Questions. In general, the common themes required are:
| JVM | Java Virtual Machine (JVM) |
| Bytecode | Java bytecode is compiled Java program, which is machine independent, and get processed by the JVM instead of the processor |
| Java Threads | With the JVM as a supervisor: – Threads can only access a resource one at the time (synchronized) – The first thread acquire the lock to the resources – The JVM supervise than no other thread access it to avoid to corrupt the resources – Once the thread release the lock, it notify the other threads waiting – The next thread start its processing and the other are sleeping until their turn to join |
| String Objects | The reason String objects are immutable (i.e. String is immutable and final in Java, and the JVM uses String Pool to store all the String objects) |
| Polymorphism | Polymorphism is the ability of an object to take on many forms. The most common use of polymorphism in OOP occurs when a parent class reference is used to refer to a child class object. |
| Polymorphism vs Overriding vs Overloading | Polymorphism is the ability of a class instance to behave as if it were an instance of another class in its inheritance tree, most often one of its ancestor classes. For example, in Java all classes inherit from Object. Therefore, you can create a variable of type Object and assign to it an instance of any class.
An override is a type of function which occurs in a class which inherits from another class. An override function “replaces” a function inherited from the base class, but does so in such a way that it is called even when an instance of its class is pretending to be a different type through polymorphism. Referring to the previous example, you could define your own class and override the toString() function. Because this function is inherited from Object, it will still be available if you copy an instance of this class into an Object-type variable. Normally, if you call toString() on your class while it is pretending to be an Object, the version of toString which will actually fire is the one defined on Object itself. However, because the function is an override, the definition of toString() from your class is used even when the class instance’s true type is hidden behind polymorphism. Overloading is the action of defining multiple methods with the same name, but with different parameters. It is unrelated to either overriding or polymorphism. |
| super() | super() calls the parent constructor with no arguments. It can be used also with arguments. I.e. super(arg1) and it will call the constructor that accepts 1 parameter of the type of arg1 (if exists). I can also be used to call methods from the parent. I.e. super.method() |
| static | The static keyword in Java means that the variable or function is shared between all instances of that class as it belongs to the type, not the actual objects themselves. |
C
C is a general-purpose and imperative computer programming language. It is often used in low-level programming such as operating systems, modules, drivers, and where performance needs to be as close as possible to the hardware, such as in networking or databases.
There’s many online resources on this topic; the following resources will get you started with most of the required information: C Interview Questions. In general, the common themes required are:
| volatile | volatile keyword is a qualifier applied to a variable when declared which tells the compiler that the value of the variable may change at any time. It tells the compiler not to optimise anything that has to do with the volatile variable. |
| const void pointer | const void * points to memory that should not be modified. |
| Threads | A thread is a single sequence stream within in a process. They are not independent like processes, they share their code section, data section and OS resources like open files and signals with other threads. However, like a process, a thread has its own program counter, a register set, and a stack space. |
| Parallelism | Multi-threading improves performance, operating faster as thread creation is faster, context switching between threads is fast, threads can be terminated easily, and communication between threads is faster. |
| pthreads | Unlike Java, multithreading is not supported by the language standard. POSIX Threads (or pthreads) is a standard library to implement threads. |
| code segment | Code segment, or text segment, corresponds to the virtual address space that contains executable instructions. It is loaded from an object file into a corresponding code segment in memory. |
| data segment | Memory section which contains any global or static variables which have a pre-defined value and can be modified. It is managed by malloc, calloc, realloc, and free functions. |
| stack segment | Stack memory section contains the program stack, a LIFO structure, located in the higher parts of memory, with a stack pointer registering the top and adjusted each time a value is pushed onto the stack. The set of values pushed for one function call is termed a stack frame, which consists at minimum of a return address. |
| heap segment | Memory area shared by all threads, shared libraries, and dynamically loaded modules in a process. |
Python
Python is an interpreted high-level programming language for general-purpose programming. Its uses are extensive, from system scripting to large websites, it is really popular and versatile.
There’s many online resources on this topic; the following resources will get you started with most of the required information: Python Interview Questions, Essential Python Interview Questions, Common Python Interview Questions.
In general, the common themes required are:
| iterators, decorators, and generators | – Iterator objects are required to support two methods while following the iterator protocol, __iter__ and _next__. – Decorator are a way to dynamically add some new behaviour to some objects. – Generator are an easier way to create iterators using a keyword yield from a function. |
with |
with keyword is used when working with resources to ensure it is “cleaned up” on completion, even if exceptions are thrown. |
| list vs tuple | The difference between list and tuple is that list is mutable while tuple is not. Tuple can be hashed for e.g as a key for dictionaries. |
| set vs list vs tuple vs dict | A list keeps order, dict and set don’t: when you care about order, therefore, you must use list (if your choice of containers is limited to these three, of course;-). dict associates with each key a value, while list and set just contain values: very different use cases, obviously. |
new_list = [expression(i) for i in old_list if filter(i)] |
Syntax for a list comprehensions, which provide a concise way to create lists. |
'%s@%s' % (user, host) # 'username@host''{0}@{1}'.format(user, host) # 'username@host' |
Strings concatenation syntax recommend for 2 or more strings |
| Monkey Patching | In a unit test, you don’t want to depend on the external data source – so you dynamically replace the get_data method with a stub that returns some fixed data |
| python -m pdb script.py | Runs a script with Python DeBugguer (PDB), with for available methods run(), runeval(), set_trace() and others |
import csvwith open('file.csv', 'rb') as f: contents = csv.reader(f) for row in contents: print ', '.join(row) |
Snippet of code to read a CSV file and print its contents line by line |
import jsonwith open('file.json', 'w') as f: json.dump(result, f) |
Code snippet to write JSON contents to a file |
Systems
General knowledge
Research to show familiarity with OS troubleshooting, solving basic networking issues, and resolving database performances issues.
Linux
Linux is a family of free and open-source software operating systems built around the Linux kernel which is distributed as a distribution built around the GNU tools. It is really popular and is used nearly everywhere, from small hardware to large websites.
There’s many online resources on Linux; the following resources will get you started with most of the required information: Linux Interview Questions, Linux SysAdmin Interview Questions, General Linux Interview Questions, Unix Interview Questions And Answers .
| Kernel | The Kernel is the core of a computer’s operating system. It has complete control over everything in the system, and is the first program loaded on start-up (after the bootloader). It orchestrate the hardware and software interractions. |
| ifconfig | Tool for configuring, controlling, and querying network interface parameters. |
| traceroute | traceroute is a computer network diagnostic tool for displaying the route (path) and measuring transit delays of packets across a network. It uses ICMP echo requests and the time-to-live (TTL), or hop limit, is used to determine the routers being traversed. |
| nscd | name service cache daemon (nscd) is a daemon that provides a cache for the most common name service requests |
| boot sequence | BIOS, MBR, GRUB (or other loader), Kernel (grub.conf,/sbin/init, initrd, RAM), Init (etc/inittab), Runlevel (/etc/rc.d/rc*.d/) |
| Process ID of init | Process ID 1 is the init process responsible for starting and shutting down the system, while swapper and sched have process ID 0, and are responsible for swapping and paging. |
| Orphan Process (aka zombie) | An orphan process is a process whose parent process has finished or terminated, though it remains running itself; it will be immediately adopted by the special init system process. |
| Process Creation | The creation of processes can be either done using the fork and exec mechanism, as explained in details in this article. Forking create a exact copy of the parent as a child process with a different PID, and the address space is then populated using an exec call. |
| Process State | The state of processed can be retrieved by using the command ps to list processes (with your favourite options such as ps -aux, ps -wuxa or ps -ef). The different possible states are: – R running or runnable (on run queue) – S interruptible sleep (waiting for an event to complete) – D uninterruptible sleep (usually IO) – T stopped, either by signal or by being traced – Z defunct (zombie) process, terminated but not reaped by its parent – X dead (should never be seen) – W paging (obsolete since 2.6.xx kernel) |
| Process signals | Signals are notifications sent to a process or a thread to notify of an event. the most command one are: SIGINT (sent when pressing CTRL+C), SIGTERM (graceful kill), SIGKILL (kill -9). Extensive explanation in this Wikipedia article. |
| inode | An inode is a data structure on a filesystem that stores all the information about a file except its name and its actual data. Each inode stores the attributes and disk block location of the object data located in the data store section of the filesystem. The filesystem can run out of inodes, ‘df -i’ will show that. Details of an inode can be retrieved using the stat command. |
| Symbolic Link | A symbolic link is a link to another name in the file system. If you delete the destination file, the symbolic link won’t point to anything. |
| Hard Link | A hard link creates another file (a copy) with a link to the same inode. When the file destination file is deleted, the hardlink still exists and has contents. |
| swappiness | Linux kernel parameter defining how much and how often the kernel will copy RAM contents to swap. |
| Linux out-of-memory (OOM) killer | Linux process that reclaims over-allocated memory. It can cause issues with mission critical systems such as database, although it may be adjusted using vmstat and sysctl. |
| Disk Space | df or du, both shows disk usage, but df will report file opened then removed by a process as taking storage. df -i shows inodes usage, it can vary with df output if it has many small files indexed. |
| Sticky bit | A sticky bit is a permission bit that is set on a directory that allows only the owner of the file within that directory or the root user to delete or rename the file. No other user has the needed privileges to delete the file created by some other user. This is a security measure to avoid deletion of critical folders and their content (sub-directories and files), though other users have full permissions. |
| fdisk -l | Lists all the available partitions on the system |
| CTRL-Z + CTRL-D | Process in background and stop process |
| ldd /path/to/program objdump -p /path/to/program |
Display libraries dependencies |
| strace | Monitors system calls and signals of a specific program, to debug the execution of a program from start to end. |
| perf | Performance analyzing tool to profile application. |
| strings | Print the strings of printable characters in files. |
| sysctl | Tool to tune kernel options such as memory or size of packets to improve performances. |
| readelf | Tool to read information inside a Executable and Linkable Format (ELF) file. objdump can also provide some of the same information. |
| GNU Automake | Programming tool to automate parts of the compilation process by easing usual compilation problems such as dependencies. |
| uname -r cat/etc/*-release |
Identify current distribution |
| uname -a lshw dmidecode cat /proc/cpuinfo |
Identify current architecture, hardware, processor |
| NAS | Single storage device |
| SAN | Local network of multiple storage devices |
| chroot jail | A chroot jail is a way to isolate a process and its children from the rest of the system. It should only be used for processes that don’t run as root, as root users can break out of the jail very easily. |
| compgen -abck | grep ‘^..$’ | Look up all the two letter unix commands on your system. |
| How to recover from ‘chmod -x /bin/chmod’ | cp /bin/ls to tmp and chmod on top then back, or use python or perl to chmod |
| Recover a Apache log file | Copy the file from virtual file system attached to the process PID |
| Stop a fork bomb | pkill -f : or killall -KILL username |
Additionally, myriad of online books are available to extend the knowledge further, such as Linux Kernel in a Nutshell, Linux Kernel Module Programming, and Linux Internals Blog.
Internet
Fundamentals
The Internet is the global system of interconnected computer networks that use the Internet protocol suite (TCP/IP) to link billions of devices worldwide.
DOM
The DOM defines a standard way for accessing and manipulating XML or HTML documents, by presenting its contents as a tree-structure.
Selectors
In CSS, selectors are patterns used to select the element(s) to which a set of CSS rules apply. There are a wide variety of selectors available, allowing for fine grained precision, such as by id, class, attributes, and multiple others.
Web Services
A web service is utilised for machine-to-machine communication transferring machine-readable file formats such as XML and JSON.
SOAP
Simple Object Access Protocol (SOAP) is a messaging protocol specification for exchanging structured information to implement web services in computer networks. It uses XML for its message format, and relies on application layer protocols, mostly HTTP and SMTP for message negotiation and transmission. It offers builtin security and robustness for communication failures.
Rest API
Representational State Transfer (REST) is an architectural style that defines a set of constraints and properties based on HTTP, it is used to provide RESTful web services. Requests and responses may be in HTML, XML, or JSON, and the operations available are the predefined CRUD HTTP methods, such as GET, POST, PUT, DELETE. It was created to put services on the Internet, and is generally lighter, faster than SOAP, and support more formats.
Network
OSI & TCP/IP model layer
The TCP/IP and OSI network model layers:
- Layer 7 – Application: Provides a network interface for applications
- Layer 6 – Presentation: Translates data to a standard format
- Layer 5 – Session: Establishes sessions between communicating applications
- Layer 4 – Transport: Provides error and flow control
- Layer 3 – Network: Supports logical addressing and routing
- Layer 2 – Data-link: Provides an interface with the network adapter
- Layer 1 – Physical: Converts the data into the stream of electric to send across (the wire)
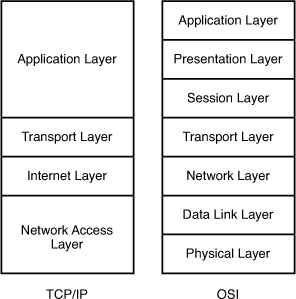
TCP/IP
Transmission Control Protocol (TCP) corresponds to the transport (Layer 4) and some session functions (Layer 5) of the OSI model. Internet Protocol (IP) corresponds to a subset of the network layer (Layer 3). It is used to send packets with acknowledgement of reception by the remote host.
UDP
User Datagram Protocol (UDP) corresponds to the transport (Layer 4) of the OSI model. It is used to send datagram over the network but, unlike TCP,the next packets are sent without the remote host doesn’t acknowledging reception.
DNS
DNS, or domain name system, is the protocol on the internet that turns human-comprehensible website names into addresses understandable by machines. DNS process looks up for the destination address in a really short time, then the client computer connects directly to the destination server, leaving the DNS server free to deal with another request.
When the query is emitted by a client, by typing the address in a browser or from a service, it asks first the operating system to connect to the configured DNS server. The DNS server is identified using the ARP protocol to map its IP address to its physical location. The query is transported from the client using TCP/IP where it will leave the current private network to be sent over the internet to destination server which can be located anywhere around the world. The query leaves the computer then pass through the local network via the switches on the LAN, then exiting by the modem to join the ISP network, to the destination network, where the DNS server is likely to be a cluster of server behind a load-balancer with rules set in the firewalls to define who is allowed to access what. A destination server can be in fact located on the same network, in this case the query is routed locally without reaching the ISP network.
ARP
ARP, or Address Resolution Protocol, is the protocol which operates below the network layer as a part of the interface between the network and the link layer. The term address resolution refers to the process of finding an address of a computer in a network.
If an IP address is not found in the ARP table, the system will then send a broadcast packet to the network using the ARP protocol to ask who as a specified IP address. Because it is a broadcast packet, it is sent to a special MAC address that causes all machines on the network to receive it.
MTU
The Maximum Transmission Unit (MTU) determines the maximum size of each packet in any transmission. The packet or frame size, specified in octets (eight-bit bytes) sent in a packet, frame, across the Internet network (TCP).
TCP 3-way hand shake
A TCP 3 way handshake occurs when establishing a connection between a client and a server:
– Client sends a SYN data packet, asking if the server is open for new connections
– Server receives the SYN packet from the client, it responds a SYN/ACK packet if it has open ports available
– Client receives the SYN/ACK from the server, and responds with an ACK packet
SSL
Secure Sockets Layer (SSL) is a standard for establishing a secure and encrypted connection between a client (browser) and a (web) server, ensuring all data passed remain private and integral.
SSL Hand Shake
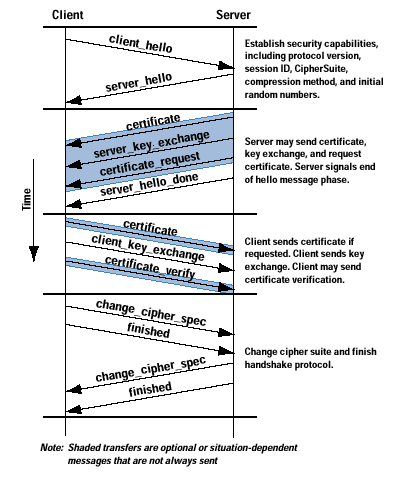
Common recruitment process
Coding Challenges
A good way to become familiar to the tools used and the questions asked during the technical interview is to attend online coding challenges.
There’s plethora of online Tools are available, but are all more or less similar. It is good to try a few to get a taste of the type of challenges offered.
Amazon
Working for Amazon, and Amazon Web Services, is focused around 12 Principles:
- Customer Obsession
- Ownership
- Invent and Simplify
- Are Right, A Lot
- Learn and Be Curious
- Hire and Develop the Best
- Insist on the Highest Standards
- Think Big
- Bias for Action
- Frugality
- Earn Trust
- Dive Deep
- Have Backbone; Disagree and Commit
- Deliver Results
The interview process is demanding, focused around coding exercise (e.g. parsing logs) and onsite interviews. Deep knowledge of all aspect of a service can be assessed, such as asking how you would build your own Amazon.
The Facebook process is very similar to Amazon and also really demanding. It focus around coding exercise (e.g. merge csv files) and onsite interviews. Below are some resources to prepare for their process:
Google is notoriously a difficult company to interview for. They have a long process which can be really demanding. Below are some resources to prepare for their process:
- Interviewer point of view
- Google SRE Interview Experience
- Solving Google Python 2 Coding Interview
- Preparing for the SRE Interview
- What SRE do?
- SRE Presentation
Resources
- https://biginterview.com/blog/2013/09/behavioral-interview-questions-conflict.html
- https://serverfault.com/questions/225946/what-are-your-best-senior-level-linux-interview-questions
- https://biginterview.com/blog/2017/04/greatest-accomplishment-question.html
- https://www.verisign.com/en_US/website-presence/online/how-dns-works/index.xhtml

